Automatic search of VK passwords. Brute force password recovery. Programs for Brutus
Brute force - brute force, brute force hacking
In the article "" it was said that hacking VK using brute force (program) is impossible.
This is not entirely true, there are still loopholes...
Below is a working script, but first...
At the bottom of the article is a free program for generating a brute dictionary and a listing of “top sucker passwords”
I make a reservation in advance that we are talking about a classic “brute force” without any PBKDF2 algorithms, without parsing sha hashing, because at the everyday level this is an overwhelming task.
There are many programs circulating on the Internet “for hacking VK using brute force (brute force)”
Which one to choose? Which one will help (without harming me)?
- None
Each VK account requires a personal approach and template programs from the network are all crap, scam, bullshit.
Now you will understand why. Mathematical part briefly.
The minimum length of a VK password is 6 characters.
The password must contain:
numbers(0-9 - 10 options),
letters(a-z - 26 in Latin),
capital letters(A-Z - also 26)
Total for each symbol - 10+26+26=62 (!) options, so the number of combinations for:
6 character password - 56,800,235,584 (56.8 billion)
7 character password - 3,521,614,606,208 (3.5 trillion)
8 character password - 218,340,105,584,896 (218 trillion)
9-character password -13 537 086 546 263 600 (HZ as it is called))))
We don’t know the length of the password, so we’ll have to brute force a range of at least 6-8 characters
Total: 6+7+8 characters = 221,918,520,426,688 (222 trillion) options
Let's say you have a fairly good computer, but the question arises - how many requests to the VK server can it make?
What is the search speed of a home computer?
Let's do the math. To do this, open the command line (Start - standard - Command Prompt or launch the cmd.exe process)
Enter the command and get the server response
“Response from .....time 134ms” (this is for me, your time may differ)
Ping time is the time it takes for the signal to travel from our machine to the server and back
There are 1000 milliseconds (ms) in one second, so
Brute speed from your machine (requests/sec) will be = 1000/response time
In my case, 1000/134ms = 7.4 requests (passwords) per second
How long will it take to search passwords for VK?
Let me remind you that we are trying out 221,918,520,426,688 (222 trillion) password options.
Therefore, to find out how much we will crack the VK password by brute force, we divide the amount by the speed, i.e.
221918520426688 passwords / 7.4 passwords per second = 29737081737176sec = 495618028953 min = 8260300483 hours = 344179187 days = 942957 years
Conclusion:a real program for hacking VK could find a password by brute force in 94 thousand years.
Question: What about the videos on YouTube in which miracle programs brute-force a VK page in a few minutes/hours?
I answer: This is a scam created with the goal of infecting your computer to steal your own data. No more no less.
You can significantly speed up the search process!
To do this you need:
1. Increase computing power. For example, infect 1,000,000 other people’s computers and simultaneously brute force VK from all of them (that’s funny)
2. Shorten the Brute dictionary to, for example, a couple of thousand (based on the principle of social engineering)
How to make a Brute dictionary?
1. Using pens in the notepad program (notepad.exe)
2. Prog “brutus generator” (link at the bottom of the article)
We fill this brute-dictionary with real options.
Real ones are those that are at least somehow connected with the person being hacked:
-phones(him, his relatives, friends)
Example- numbers with +7c, 8c, without 8c - rarely seen
- dates of birth(him, his relatives, loved ones)
Example- (same date) 010118, 01012018, 20180101, 180101 - comes across often
- Names of loved ones
Example- SashaMaria, MariaIvanova, SaNoMaIv - comes across average
Site name (or last name) on a different layout
Example, if you type the word “vkontakte” on the Russian keyboard, you will get “mlshtefleu” - such a scheme very often comes across on all sites.
- Lokhov's list of passwords for Brutus(list of the most common passwords on the Internet - link at the end of the article)
How long does it take to write a dictionary? Well, not really - half an hour is enough. Who said it would be easy?))
Let's say we have a created brute dictionary and a working program for selecting a VK password (or manually entering it using a dictionary).
One important problem arises - the server security system.
Actually, its hindrance lies in the fact that if the requests are too frequent, the server stupidly blocks (temporarily) your IP. In addition, if you work with VK through a standard input form (HTML\FORM), then after the 3rd unsuccessful attempt, VK will ask you to enter a captcha.
In the old version of VK, you could simply switch to the mobile version - m.vk.com, but now there is no mobile version as such - in 2016 they made a single adaptive design.
How to bypass VKontakte captcha?
VK requires entering a captcha after 3 unsuccessful attempts (rebooting F5 does not help), but how does it know that it's you Are you trying to log in multiple times?
By IP
- by cookies, cache and JavaScript
There are no problems with cookies, cache and JavaScript - you can simply disable them in your browser settings.
IP can be changed by installing a program for changing IP - there is nothing complicated about it, there are plenty of them on the Internet (Google can help)
You can use the TOR browser (for those who don’t know, this is a browser for anonymously surfing the network, it also changes IP numbers with each new session, a useful thing especially for those who surf or work in SAR)
But all attempts at brute force are almost completely nullified by GEOLOCATION.
The VK server remembers where (geographically) the last login was made.
And if your IP is from another locality, then (possibly) the following message will pop up:
"You are trying to log in under the name Ivan Ivanov from an unusual place."
To confirm that you really are the owner of the page, please provide all the missing digits of the phone number to which the page is linked.
Script for brute web forms (such as a program for hacking VK)
Important!
On the VK server there is a script that monitors the frequency of sending packets, i.e. if you hammer at a speed of N times/sec, you will automatically be sent to the IP ban list.
VK also uses GEO tracking.
Without a dynamic IP, you shouldn’t try to brute, a VPN can help.
Personally, I consider brute-forcing VK passwords to be unpromising, but for connoisseurs I’ll post an old Perl script borrowed from 5p4x2knet a.k.a. Apocalyptic's and a little fixed.
The script works using the POST method only in two parameters - login And password.
If the login is known (for example, a phone number), then simply fill in the corresponding fields with the value without referring to the dictionary.
Hidden fields - captcha, the script will not transmit images, hide the source of requests (yourself) as described above.
Here we will need the sane Brute dictionary that we compiled at the beginning of the article. (let's call it, for example, brutal.txt )
We also need a file from which our program will receive information.
The program will brute force all scripts specified in this file.( info.txt). If there is only one script, then you can replace
Naturally, the file for recording the results ( result.txt)
So,
{
#connect the object
$usagent = LWP::UserAgent
#open the file with information (if we can’t open it, we exit);
# dump the file into the @infa array and close it. (if there is only one script, then you can immediately specify it)
open(INFA, ";
close(INFA);
#open the Brute dictionary
open(BRUT, ";
close(BRUT);
#opening a file with results (appends to the end).
open(RESULT, ">>$ARGV");
#beginning of the cycle
foreach $name (@infa)
{
#separate URL, login, variables and error information
($url, $login, $log_vr, $pwd_vr, $failed) = split(//, $name);
#show URL
print "$url...n";
#start another cycle
foreach $brut (@brut)
{
#kill spaces and line breaks
$pss =~ s/ //;
$pss =~ s/n//;
#connect a new object
$usagent = LWP::UserAgent->new();
#creating requests.
$req = HTTP::Request->new(POST=>$url);
$req->content_type("application/x-www-form-urlencoded");
$req->content("$log_vr=$login&$pwd_vr=$pss");
#and its sending
$result = $usagent -> request($req);
#storing the results to a variable
$res = $result->content;
#if it doesn't work, an error message is generated
if($res!~ /$failed/i)
{
#output message with password; record in results;
print "brutword found. It isn't$pssnn";
print RESULT "URL: $urlnLOGIN: $loginnBRUT: $pssnn";
#otherwise continued selection
last;
}
}
}
#closing the result.txt file
close(RESULT);
We recently published an article about password strength and passwords that are used by many users. Most people use weak passwords. But how can you make sure your password is strong? Password cracking is an integral part of digital forensics and information security testing.
In this article, we have compiled the best password cracking programs that can be used by system administrators to check the strength of their passwords. All utilities use different algorithms and are applicable to different situations. Let's first look at some basic information that will help you understand what we'll be dealing with.
In the field of cybersecurity and cryptography, password cracking plays a very important role. It is the process of password recovery to compromise or restore the security of a computer or system. So, why do you need to learn password cracking programs? For peaceful purposes, you can use password hacking to recover forgotten passwords from online accounts, and this is also used by system administrators for prevention on a regular basis.
In most cases, brute force is used to crack passwords. The software generates various password options and reports if the correct one was found. In some cases, a personal computer can produce millions of options per second. The program for cracking a password on a PC checks all options and finds the real password.
The time required to crack a password is proportional to the length and complexity of that password. Therefore, it is recommended to use complex passwords that are difficult to guess or guess. Also, the brute force speed depends on the cryptographic function that is used to generate password hashes. Therefore, it is better to use Bcrypt for password encryption rather than MD5 or SHA.
Here are the main password guessing methods used by attackers:
- Dictionary attack- the attack uses a file that contains a list of words. The program checks each of the words to find the result;
- Bruteforce attack- you don’t have to use a dictionary, but rather iterate through all combinations of given characters;
- Rainbow Table Attack- the attack uses pre-computed hashes, so it is faster.
There are other methods of cracking passwords based on social engineering, but today we will focus only on attacks without user interaction. To protect against such attacks, you need to use only complex passwords. Now let’s look at the best tools for cracking passwords in 2017. This list is published for informational purposes only and we in no way encourage you to hack other people’s personal data.
The best password cracking programs
1. John the Ripper
John the Ripper is one of the most popular password cracking tools available to absolutely everyone. It is open source and written in the C programming language. Here are various methods for brute-forcing passwords.
The program is capable of searching passwords using a saved hash, and supports various hashing algorithms, including automatic algorithm detection. John the Ripper is part of Rapid7's security testing toolkit. In addition to Linux, Windows and MacOS are supported.
2. Aircrack-ng

Aircrack-ng is a set of programs for hacking and intercepting passwords from wifi networks. The program is one of the best that is used by hackers. Here you will find everything you need to crack WEP and WPA encryption, from intercepting the hash to obtaining a ready-made password.
WEP encryption is especially easy to crack; to overcome the protection, there are PMS and PTW attacks, with which you can crack this protocol in a matter of minutes if there is sufficient traffic flow through the network. So always use WPA2 to be safe. All three platforms are also supported: Linux, Windows, MacOS.
3.Rainbow Crack

As the name suggests, RainbowCrack uses rainbow tables to crack password hashes. Using ready-made tables, the utility greatly reduces hacking time. In addition, there are both GUI and command line utilities.
After completing the preliminary calculations stage, this tool works hundreds of times faster than with conventional search. You don't need to create the tables yourself; the developers have already created them for LM, NTLM, MD5 and SHA1. Everything is available for free.
Another important point is GPU acceleration. By using a video card, you can reduce the password calculation time by several orders of magnitude. Windows and Linux platforms are supported.
4. THC Hydra

Unlike the programs listed above, Hydra works differently. It does not calculate hashes. Instead, the program performs brute-force attacks on various network protocols. Astrisk, FTP, HTTP, MySQL, XMPP, Telnet, SHH and many others are supported here. The main purpose of the utility is brute force attacks on the password entry form.
This tool helps security researchers find out how easy it is to gain access to a remote system. Modules can be added to expand functionality; Linux, Windows, Solaris, FreeBSD and MacOS are supported.
5. HashCat

According to the developers, this is the fastest tool for brute force passwords. It is distributed as free software and supports the following algorithms: md4, md5, LM, SHA, MySQL, Cisco PIX and Unix Crypt.
There are versions of the tool for brute force on the CPU, as well as GPU-based hacking - oclHashcat and cudaHashcat. In addition to the standard Bruteforce attack, dictionary attacks, hybrid attacks using most, tables, Prince, and so on are supported. Platforms supported are Windows, Linux and MacOS.
6. Crowbar
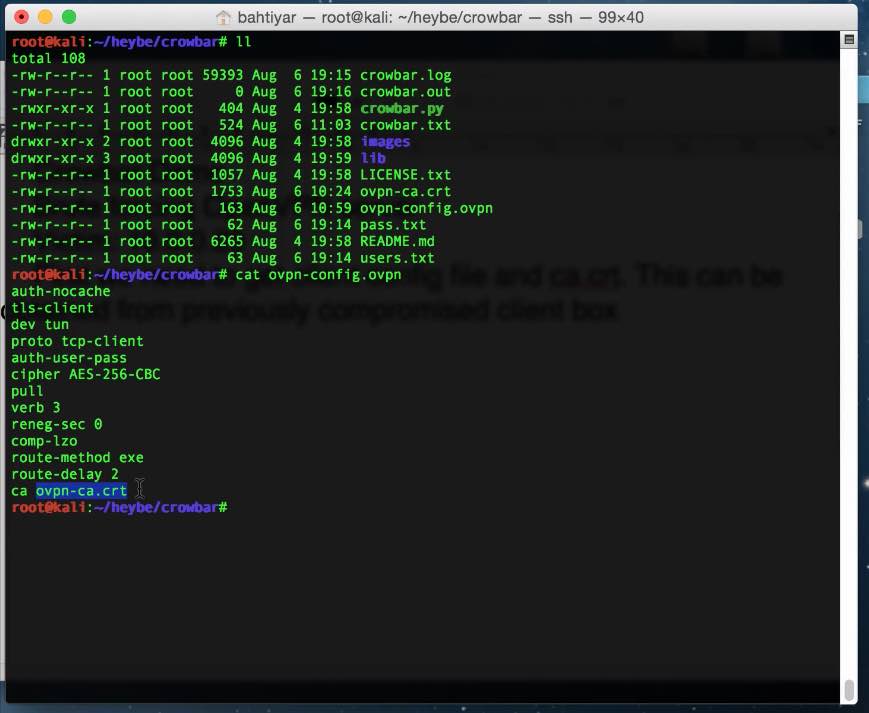
Crowbar is a popular password security testing tool. Other password brute-force programs use usernames and passwords, but crowbar allows you to brute-force SSH keys.
This open source tool is designed to work with protocols that are rarely supported by other programs. Currently supported are VNC, OpenVPN, SSP, NLA. The program can run on Linux, Windows and MacOS.
7.coWPatty

This is an implementation of a utility for brute-forcing a WPA/WPA2 PSK password based on a dictionary or rainbow tables. Using rainbow tables greatly speeds up the operation of the utility. The PSK standard is now used very often. The only good thing is that it is very difficult to guess the password if it was initially chosen correctly.
The use of VK password guessing programs is used for the following purposes: stealing an account to send spam and intrusive advertising, obtaining personal information by an interested party about a specific user, logging into a personal page if there is no way to recover the password. It’s no secret that a user’s VKontakte page stores his personal data, personal messages, photo, audio and video materials. To ensure that confidential information remains protected, when choosing a password for your own account, you should be guided by knowledge of existing programs for hacking it. This article is dedicated to introducing the reader to the most popular means of stealing a page on a social network.
Programs for selecting passwords from VKontakte pages
The social network VKontakte has millions of users, and this number is growing every day. The increase in this figure forces developers to constantly improve the security system. This is due to the fact that interest in hacking pages is proportional to the number of network users. There can be many reasons for hacking a personal page, and for these purposes a large number of different software have been developed, differing in functionality and hacking method. These could be programs for selecting a unique combination of symbols, for tracking actions via the Internet, etc.
In order to protect your page from hacking, below are the most popular programs for gaining access to your personal page, after reading which you can check your password for security or generate a new unique key to log in to the system. If you are aiming to hack someone else's page, you need to remember that in accordance with the criminal code of the Russian Federation ( Criminal Code of the Russian Federation Article 272) this action is a crime and entails criminal liability.
Online password generator
This method of hacking is used by those who want to obtain the personal data of a specific user (an acquaintance).
The essence of the method is that knowing the login (email or mobile phone number) from the account of the interested person, all that remains is to select the login key. Selection occurs in two ways:
- Manual search. Many users of the social network do not pay special attention to their own security, and when creating a login password, they operate with such information as: last name and first name, nickname, date of birth, favorite number or date, etc. Such a page is quite easy to hack by studying the information on it or knowing the person personally.
- Automatic search. Involves the use of a special software product. The most popular site for automatic search is Online password generator. The essence of this system is that using tags, keywords are generated, on the basis of which a password is selected. It should be noted that the Online Generator can be used not only for account recovery/hacking, but also for generating unique keys for logging into various personal accounts and pages.

Vklom 3.1
Vklom 3.1 is a special program designed to gain access to the personal page of a user of the well-known social network VKontakte. It should be noted that the program does not hack someone else’s account, but only simulates the process of logging into a personal page. Its main feature is a clear interface and minimum system requirements (Windows Vista, XP, 7, 8, 8.1, 10, there is a version for Android).
VK Hack 2.2
The VK Hack 2.2 utility is designed to effectively select keys to personal pages for specified accounts. The mechanism of the program is to select a combination of characters for a given Id using its own database. The effectiveness of this program is 50%, the selection time is several hours. Feature of the program: the presence of additional functions for increasing likes, subscribers, gifts, and so on.
John the Ripper
John the Ripper is the most popular software on the topic under consideration. The utility is open source and has a number of brute force methods (brute force, selection using a dictionary, etc.). It is often used to assess the strength of passwords (account security level) on Windows, MacOS and Linux, as well as Android. The lack of a graphical interface makes the program difficult for inexperienced computer users to use.
Aircrack-ng

Aircrack-ng is a tool used by hackers to hack and obtain the access code to the victim’s personal page via a Wi-Fi network. The program's action is based on intercepting a hash or obtaining a ready-made password using PMS and PTW attacks. Aircrack-ng works on Windows, MacOS and Linux. You can protect yourself from this type of hacking using WPA2 encryption type.
RainbowCrack
The main advantage of RainbowCrack is the availability of ready-made tables for hacking, which increase the speed of obtaining the desired result several times. The utility implies the ability to speed up the search process using the GPU (graphics processing unit). Only Windows and MacOS users can use RainbowCrack.
THC Hydra
THC Hydra is a console application for “calculating” the password for the login form on your personal VKontakte page and more. Supports protocols: Astrisk, Cisco auth, AFP, HTTP, HTTP-Proxy, HTTPS-FORM-POST, IMAP, MySQL, Oracle SID, POSTGRES, TS2, SNMP v1+v2+v3, SOCKS5, RDP and others. Compiles on Windows, Linux, Solaris, FreeBSD, QNX and OSX. The advantage of the program is the speed of its operation and the availability of files with names/passwords, but its main disadvantage is the complex interface for inexperienced users.
HashCat

The freely available cross-platform HashCat program is gaining increasing popularity. It captivated many both with its time of selecting a key to enter, due to the use of both a video card and a central processor, and with an impressive list of supporting attacks: Bruteforce, by dictionary, tables, mask, etc. Provides the ability to crack a password via a Wi-Fi network or from WEB application hashes.
Crowbar
Crowbar is a script in a programming language Python, which provides the ability to perform password security checks. Its main difference is the use SSH-key(s), which allows you to use any private keys obtained during penetration testing to attack other SSH servers. Advantage: support for rare protocols (VNC, OpenVPN and NLA). Compiles on Windows, Linux and MacOS.
coWPAtty
coWPAtty - a tool for dictionary/hybrid attacks on the network "WPA/WPA2". This product is included in the software package "BackTrack" and if there is a pre-calculated PMK document for the SSID, it allows for a so-called “accelerated attack”. It's worth mentioning that coWPAtty can use "dictionary words" from John the Ripper's dictionary.
Peculiarities
The software discussed above have some differences, but lead to the same result. All of them have a number of the following features:
- The speed at which passwords are brute-forced depends more on the characteristics of the hacker’s PC than on the program itself. For example, Pentium II and III provide search speeds of about 2 million/sec;
- An entry code consisting of more than 10 characters will require more time from any of the listed programs;
- Availability of various attack methods and protocol support.
- Most of the software is freely available and completely free.
- They can be blocked by antivirus programs despite the trusted source.
A common occurrence on the Internet. It is carried out for different purposes. The most common goal is sending spam and intrusive advertising. Sometimes hackers steal money from accounts on social networks. Hacking of payment systems is dangerous. Hacking an email password, in addition to sending spam, carries the danger that all other account data can also be found out. Sometimes it is carried out for the purpose of stealing game content.
Password cracking methods
Even the best email passwords can be hacked. The ways in which hackers operate are improving every day. These are special programs for selecting combinations, methods for tracking actions on the Internet, etc.
Phishing
This method of finding out the password from VK or another social network is popular among hackers. The user is sent a message asking them to go to a site that looks similar to the one the hacker is trying to hack. Usually, it is completely copied from it.
After clicking on the link, the user enters other data, thinking that he is trying to log into his usual account. You can get to such a site and try to find out the password, having a login, that is, using the “Account Recovery” function.
The user clicks the “Login” button and the data instantly goes to the attackers. The user himself is redirected to the page of the real social network, without even noticing what happened. Advanced social engineering allows hackers to find out the password of another person's contact.
After all, in order for a user to click on a fake link, it is necessary to “earn” his trust. The method is not very effective, but easy to implement. However, the account owner may suspect that the real one is often not much different) and refuse to switch. The attacker can be easily found.
When entering your password, pay attention to the site address: attackers often make the address of a fake site look similar to the original siteSelection
The main technology used by hackers to try to find out an email password by brute force is BruteForce. This is a method of automated generation and substitution of combinations for an account. To run such a selection, you need a special program, the password cracking of which will be quick. This program operates on a mathematical principle, where the correct solution is determined by selection.
Thus, the program endlessly generates combinations of numbers and letters and checks them for correctness. Due to their high performance, such programs work quite quickly.
A hacker service for hacking can be either universal or for a specific site. When it works, a fake proxy is created, thanks to which attackers can hide their IP. In addition, by regularly changing it, it is possible to avoid blocking the computer from which hacking is carried out. After it is hacked, when you log into your account, you will see a message stating that your password has been compromised. The following urgently needs to be done:
- Change account details;
- Change security question;
- Write to the Administration that the password in Contact (or on another resource) has been compromised.
Hacking the password of the social network VKontakte by brute forceAlthough earlier programs were used that operated according to , now more advanced ones have appeared. Now substituting numbers into a word will not make your account secure. New programs select completely arbitrary alphanumeric combinations; they can be used to crack a very complex combination of symbols.
Hashes and website hacking
An effective but complex hacking method. To find out the password, hackers hack a website that stores hashes of user code combinations. The hash is obtained after the combination of letters has undergone an irreversibly complex procedure. When you enter a combination of characters when logging into your account, the hash is calculated again and if it matches the saved one, then you entered the code word correctly. This data is stolen by attackers who hack the site. This is even simpler with old resources that store not hashes, but the letter combinations themselves.
The hash is not that difficult to decrypt. Hackers have many programs and services that allow them to recognize and use them. They can see the password in Yandex Mail, after hacking the service itself, as follows:
- Calculation of hashing algorithms and data decryption;
- Having a database of BruteForce code combinations, the hacker also has hashes of these words, encoded by one or another algorithm. The program can only compare the existing ones with the new ones;
- There are not many algorithms, and they are common.
Hashing on websites is a process similar to how cookies work on a PC. Decrypting it is as easy as finding out the password from cookies. Therefore, it is obvious that such storage is not reliable account protection even with a very complex combination.
Hacking a password by guessing it from a dictionarySpyware
Spyware is software installed on a PC that is hidden. So that the user does not know about its existence. Essentially it is a virus. Designed to collect information about the user, logins, browser request history, code words, etc. Necessary for hacking and for conducting targeted advertising. With the help of such programs, information is transmitted directly to the attacker.
Such programs disguise themselves as software that offers to copy the password in the form of asterisks or recover it from cookies. Such programs must be used with caution. It’s better to use a browser to restore the ability to log into your account. Using spyware, you can find out your friend's password by installing malware on his phone or computer. In this case, the data will be transferred to you.
The spy program does not crack the password, it simply steals it and sends it to the attackerHas your password been hacked?
Some resources show hacking notifications themselves. The social network VKontakte issues a notification that the password has been compromised when logging into your account. If you change the code word to the old one, such a notification may appear, since the site stores a black list of passwords from which spam was sent, etc.
A message window warning the user that his account has been hackedIn addition, there are a number of online services that feature accounts that have recently fallen into the hands of criminals. If there are reasons to believe that they tried to hack your email password, then enter your email address (or login, if we are not talking about mailboxes) in the field and you will see whether your account was hacked.
You can find out if your account was hacked in other ways. The main one is the analysis of activity in your account during your absence from the site.
WATCH THE VIDEO
If your friends received messages with advertising content or invitations to third-party sites, you see messages and notifications for the first time, although the site shows that they have been viewed, etc. then your page was used while you were away. However, it might not be visible online. There are programs to hide the presence of users on the network.
There are often cases when you need to come up with a rather complex and unique password using different case, numbers and letters, but creating such complex passwords takes a lot of time, especially if you need to create a large number of them.
Typically, such situations are faced by various kinds of administrators who need to create and monitor a user base or those who deal with security on the Internet and not only; the list of areas of application of such complex passwords could go on for quite a long time.
To simplify and speed up this process of coming up with passwords and logins, you can use online services or programs that can be installed and run on your local computer. It is these services that will be discussed in our article.
The list of programs will present the most popular and functional services for creating complex and simple passwords with logins. These services will be presented in two forms, for online use and as a program on a computer.
The article will present the most functional and easy-to-use password and login generators, which are completely free.
Online password generators
Password generators for installation on a computer
Login generator
LastPass...
An online service that allows you to generate a password of any length with a choice of letter case and symbols. The password is generated directly on your computer using Javascript. All passwords created using this service are not transferred anywhere and are displayed only on your computer.
This service is available not only online, it can also be downloaded and installed on a computer in order to be used locally without the need for an Internet connection.
Password creation options:
- Password length in characters
- Create a password in the form of a word, for simplified pronunciation.
- Number of digital characters in the password
- Selecting the type of characters to use (Letters of different case, numbers and special characters)
Conclusion
This article presented the most functional and easy-to-use password and login generators. You can get acquainted with general information for each generator and decide on the functionality you need.